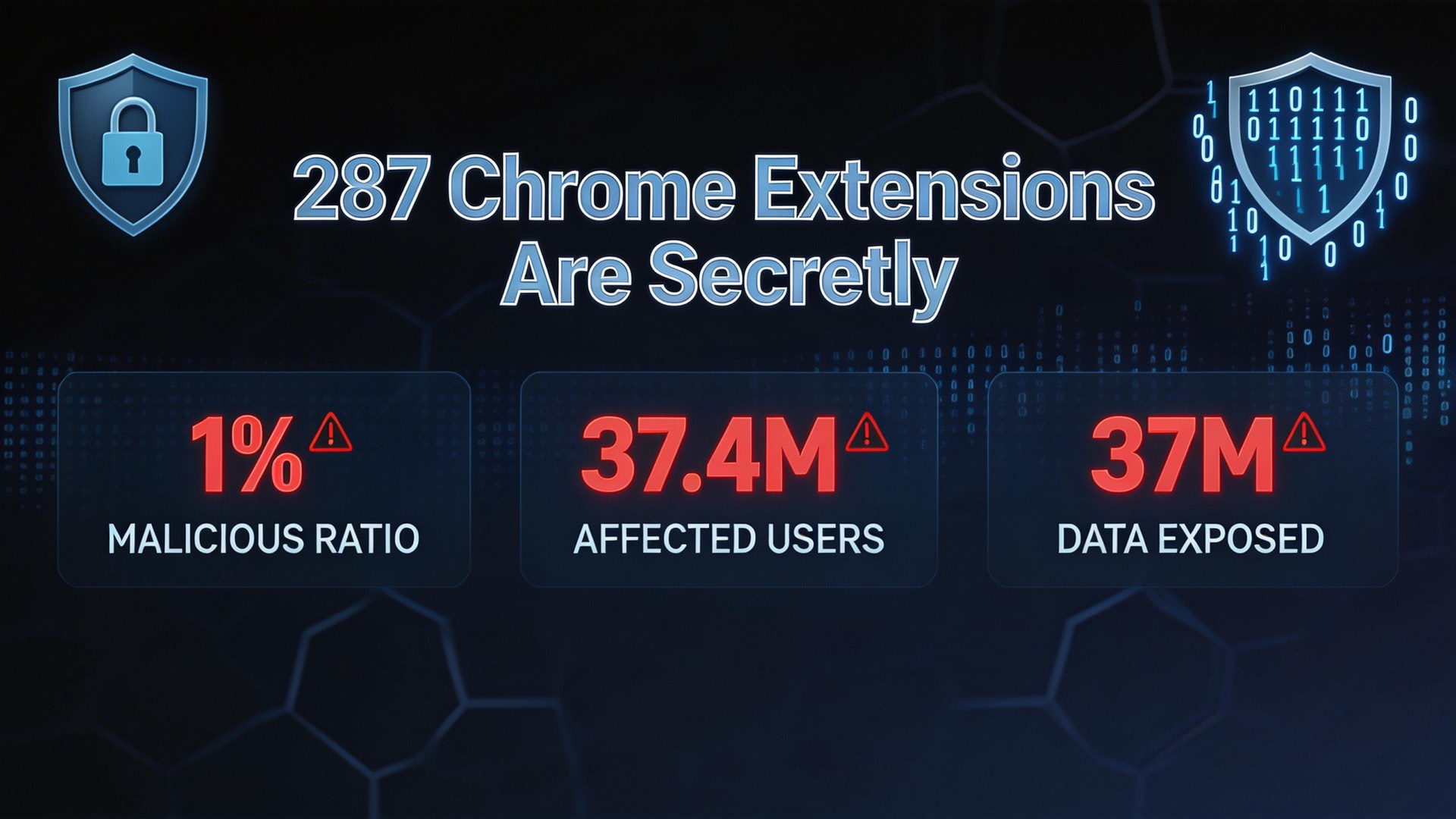
287 Chrome Extensions Are Secretly Spying on 37 Million Users
Your browser extensions might be watching everything you do online—and selling that data to the highest bidder. A systematic security analysis has uncovered a massive surveillance network hiding in plain sight inside Google’s Chrome Web Store.
The Core Insight
Security researchers built an automated pipeline to test Chrome extensions at scale. They routed browser traffic through a man-in-the-middle proxy, fed the extensions URLs of varying lengths, and measured whether outbound traffic correlated with URL size. If it did, the extension was leaking browsing history.
The results are staggering: 287 extensions are actively exfiltrating browsing history, collectively installed by approximately 37.4 million users—roughly 1% of Chrome’s global user base, or about the population of Poland.
The data collectors span from household names like Similarweb to obscure entities like “Big Star Labs” (which appears to be a Similarweb front) to Chinese actors and various data brokers. The monetization model is straightforward: sell aggregated browsing histories to ad-tech firms, or worse.
Why This Matters
The researchers went beyond detection. They set up honeypots—fake URLs that would only be visited through the compromised extensions—and watched who came calling:
- Kontera (multiple AWS IPs) emerged as the biggest scraper
- HashDit and Blocksi AI Web Filter also made appearances
- The Kontera scraper links directly to Similarweb’s extension ecosystem
Some extensions use embarrassingly weak obfuscation. Poper Blocker? ROT47 cipher—decoded in seconds. But Stylus (the theme manager) went full crypto: generating random AES-256 keys, encrypting payloads, then encrypting the AES key with a hardcoded RSA public key. Breaking that requires capturing the ephemeral AES key before it’s encrypted.
The sophistication varies, but the intent doesn’t: capture every URL you visit, package it up, and ship it out.
Key Takeaways
- 37.4M users affected across 287 confirmed leaky extensions
- Primary actors: Similarweb (and fronts like Big Star Labs), Curly Doggo, Offidocs, Chinese groups
- Data risks: Profiling, targeted advertising, corporate espionage, credential harvesting
- Detection method: If outbound traffic grows linearly with URL length, the extension is shipping your URLs
- Crypto escalation: Some extensions now use RSA-wrapped AES encryption to hide exfiltration
The scariest part? Even “benign” leakage is dangerous. Your URLs contain personal identifiers, search queries, internal company links, session tokens. In the wrong hands, that’s enough to target individuals, steal sessions, or conduct corporate espionage.
Looking Ahead
The researchers chose not to release their automated scanning pipeline, fearing it would help attackers adapt faster. But the 287 flagged extensions are documented in their public report.
The deeper lesson: any free, closed-source software makes you the product. If an extension isn’t open source, assume it’s harvesting something. The Chrome Web Store’s vetting process clearly isn’t catching these—not when a quarter-billion-dollar company like Similarweb can run a surveillance network through dozens of seemingly innocent extensions.
Review your installed extensions today. If you don’t absolutely need it, remove it. And if you keep it, assume it’s watching.
Based on analysis of “Spying Chrome Extensions: 287 Extensions spying on 37M users” by Q Continuum